KisMAC, The ultimate WIFI Stumbler
KisMAC Tutorial
KisMAC How to
1: read this page completely. Do not download it now!
2: Repeat, you’ll save and efforts!
For Mac OS Leopard 10.5 Download KisMAC 0.2.99
For Mac OS Snow Leopard 10.6+ Download KisMAC 0.3 +
KisMAC 0.3 + does not work with Leopard 10.5
KisMAC is a free wireless network discovery and has a wide range of powerful capabilities: Detection, Deauthentication, De-cloacking, Passive Scanning Mode, Re-injection, GPS, and the ability to crack WPA and WEP keys. Not to mention PCAP, CAP or Dumplogs, GPS and export multi format.
KisMAC is really powerful and leave NetStumbler in the dust.
KisMAC is not for beginners and the first step with KisMAC is to read the FAQ. The second step is to read the FAQ again. Once again: read, repeat, play. 99% of the issues are user related.
WEP Crack in passive mode
Without Re-injection device (AirPort or AirPort Extreme Card only)
Before you start, give us a little love ;-) =>
-
‣ Install KisMAC
-
‣ Start KisMAC
Go to KisMAC >>> PREFERENCES>>> DRIVERS
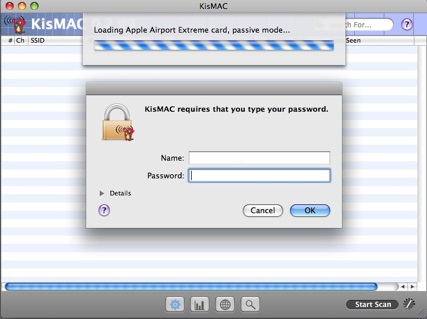
A dialog box opens and loads the driver card. An Admin password may be required.
Look for a network with a WEP key (column "ENC"), with a good signal and an active network (see "Packets" and "Data")
OR
-
• Enter "WEP" in the search box (top right) and select "ENCRYPTION" to filter the networks
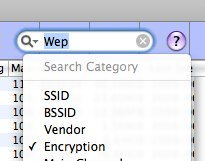
If the column ENC is "NO", the network is open: No need to crack anything.
Once you have selected a network, look at the network channel, ie 1, 2, etc ...
Back to PREFERENCES>>>> Drivers and select only the selected network ie a
In "passive" mode you are dependent on the network traffic. If the network is not very active, you may have to scan for several hours. Passive mode is like harvesting the rain: The more it rains, the more you can collect. If it does not rain, or very little ... you have to be patient. But on the other hand, Passive Mode is completely stealth, undetectable, and does not interfere with the networks
So be patient.
Let KisMAC scan to collect enough IV's (Initialization Vectors)
You need to collect a minimum of 130 000 unique IVs before starting a crack WEP 40/64
Recommended:
200,000 unique IV for WEP 40/64
1000000 unique IV for WEP 104/128
In passive mode, it may take some time ....
You can attempt with less, but there is no warranty that it will work. The more IVs, the greater your chances to recover the key.
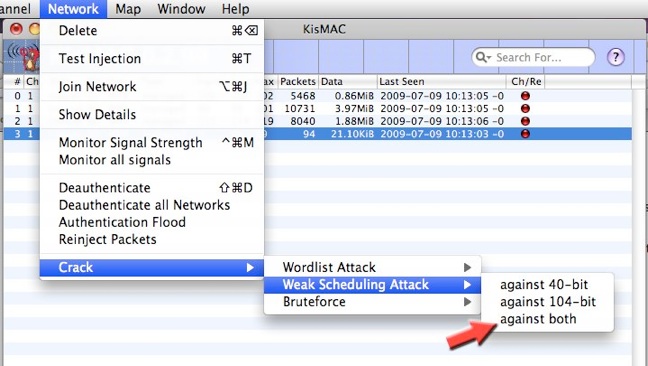
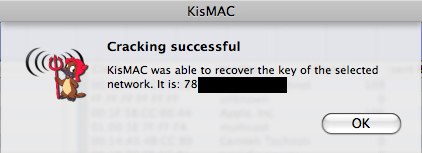
Once you have collected enough IV’s, select "NETWORK">> "CRACK">> "AGAINST BOTH"
It may take between 5 to 20 minutes, depending on your machine, for KisMAC to attempt to crack the WEP key. The fastest I have witnessed was 3 seconds.
☞ Read the notes at the end of this article.
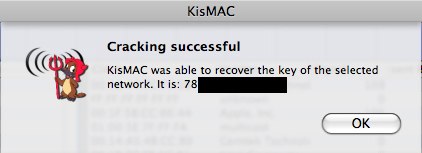
WEP Crack with Re-injection
RE-injection is a technique used to capture a certain type of packets and re-injected them in the network to artificially increases the number of IVs collected,
With Re-injection, it takes generally 15 to 30 minutes to capture enough IVs, sometimes less.
Apple Airport cards can not, to this day, re-inject packets. In order to do this you NEED a specific USB WLAN card.
Be careful here, not all cards will work: The Chipset and the type and model is what will determine success or failure.
We highly suggest that you READ the REVIEWS before buying a piece of junk.
Whatever you do, if you have an injection device (wireless card or USB adapter) Do not install the drivers for the USB card.
=> Do not install the drivers from the CD that came with the card <=
-
‣ Connect your USB card
-
‣ Start KiMAC
KisMAC tab>>> PREFERENCES>>> DRIVERS
On the main screen, select "START SCAN"
Look for a network with a WEP key (column "ENC"), with a good signal and a network of active (see "Packets" and "Data")
Once you have selected a network, look at the network channel, ie 1, 2, etc ...
Back>>> PREFERENCES>>> DRIVERS
Select only the selected network ie a
Let KisMAC scan for several minutes and determine what networks are active.
On the "Network" tab, select "RE-INJECTION Packet" and wait a bit ...
Example: KisMAC Waiting for "interesting packets"
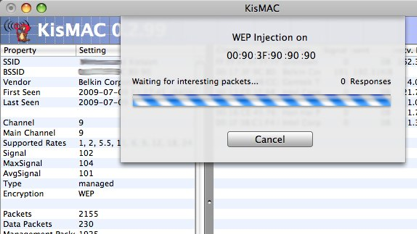
WEP Injection, 131 responses, Re-injecting
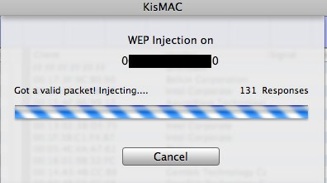
KisMAC will now try to inject packets to accelerate the process
Keep an eye on the "unique IV" number once it has reached at least 130,000 (200,000 is recommended), you can begin to consider a crack.
Once you have collected enough IV’s, select "NETWORK">> "CRACK">> "AGAINST BOTH"
It may take between 5 to 20 minutes, depending on your machine, for KisMAC to attempt to crack the WEP key. The fastest I have witnessed was 3 seconds.

Video Tutorial
Notes
For Mac OS X 10.5 Leopard Download KisMAC 0.2.99
For Mac OS X 10.6+ Snow Leopard Download KisMAC 0.3+
If you are really lost in the maze, you may consider The KisMAC School: an individual course via iChat screen sharing. 1 hour course, with all the solutions to your problems.
Classes are either in French or in English and cost about ~ 17 euros / $ 25
Details below
Keys or WEP Key
The WEP key is either 64 or 128-bit, sometimes in ASCII. The key must be entered without the semicolon. Ex: a key 70:61:62:6C:6E must be entered exactly as 7061626C6F
Alternatively, the key in ASCII stands for "pablo"
WEP 40/64 104/128
A WEP key 64-bit is in fact a 40-bit + 24 initialization bit. Calling that 64 is pure marketing. Ditto with 128-bit (104+24)
WEP 256 or 528
They exist but they are rare ....
One hour can help you save a lot of trouble
Tutoring, Via iChat, screen sharing and voice.
KisMAC for beginners, step by step.
KisMAC WEP & WPA
KisMAC Problems and Solutions
KisMAC Flood Attacks, Dehauth, etc.
Aircrack-ng native on Mac
Wireshark packet decryption
JTR (John The Ripper)
JTR bruteforce Pipe To Aircrack-ng

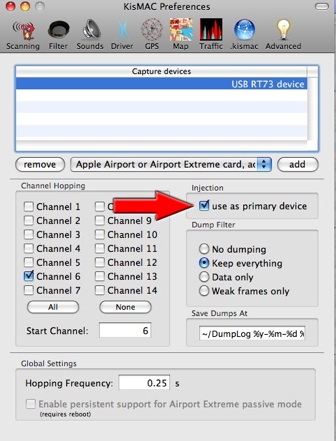
-
• Select your card driver: AirPort Extreme Card, Passive Mode
-
• Click "ADD"
-
• Select the channels, usually 1-11
channels 12-14 can create problems.
-
• Close the dialog box and select "START SCAN" on the main window
-
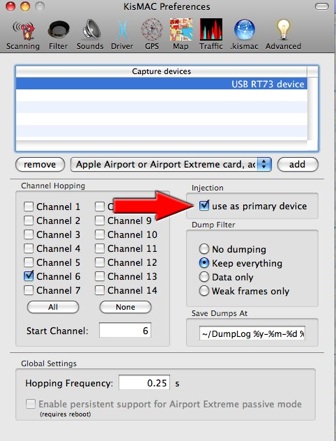
• Select your Card USB Chipset : Example: "USB RT73"
-
•Click "ADD"
-
• Check "USE AS PRIMARY DEVICE"
Select only channels 1-11 If you are in the USA, 1-13 If you are in Europe, 1-14, if you are in Japan. In some cases, the channels Ch 12-14 can create a crash: limit yourself to channels 1-11
-
• Check the "KEEP EVERYTHING"
-
• Close Dialog box